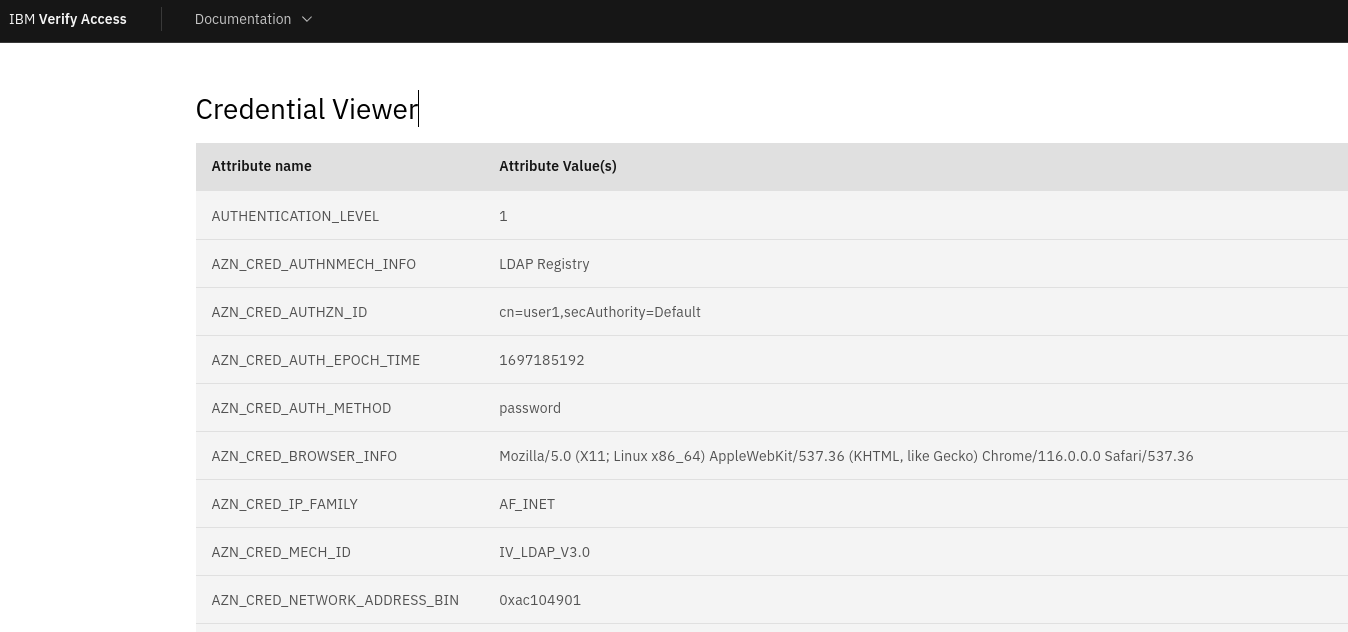
A nicer credential viewer for WebSEAL
WebSeal also has a credential viewer application, and this comes out of the box with a web interface.
That webinterface does it’s job, but it’s not very nice looking.
Based on the WebSEAL AZN decision viewer blog post, I thought it would be very simple to also provide a nicer looking Credential Viewer application.
I’ve created a very simple page based on Carbon Design, with a little javascript code.
Here’s the documentation about the cred-viewer application: https://www.ibm.com/docs/en/sva/10.0.6?topic=applications-credential-viewer-application.
WebSeal
Local application
To enable the application, add it to your WebSEAL configuration file, under the local-apps stanza.
[local-apps]
cred-viewer = credviewer
You could disable the ‘embedded html viewer’, so you’d have to use this new page.
[cred-viewer-app]
enable-embedded-html = no
ACL settings for this app
I’ve put an unauthenticated ACL on the /credviewer endpoint.
Content Security Policy
To allow the Carbon Design elements to be retrieved from the CDN, a CSP like below is necessary. Of course a better, safer way to deal with this, is to copy the sources to a location under your own control (under your own domain)
The same goes for the unsafe-inline, which you should avoid.
[acnt-mgt]
http-rsp-header = Content-Security-Policy:TEXT{default-src 'self'; script-src 'self' 'unsafe-inline' https://1.www.s81c.com/; style-src 'self' 'unsafe-inline' https://1.www.s81c.com; style-src-elem 'self' 'unsafe-inline' https://1.www.s81c.com; style-src-attr 'self' 'unsafe-inline' https://1.www.s81c.com; font-src 'self' https://1.www.s81c.com; form-action 'self'}
This was already in place, for the AZN Decision viewer in my case.
Upload the wrapper application to WebSEAL
The source files of the application are here: https://github.com/Bozzie4/blog_assets/tree/main/Isva_Carbon_Pages/credviewer.
You need:
- credviewer.js : the javascript code that performs the actual call to WebSEAL (using the Fetch API)
- credviewer.html : the html file to open
I put both these files in the pkmspublic folder in the Management Root of my reverse proxy.
This means the files are accessible by unauthenticated users (no ACL is necessary).
Example : unauthenticated
The new page is then available at https://mywebseal.domain.tld/pkmspublic/credviewer.html.
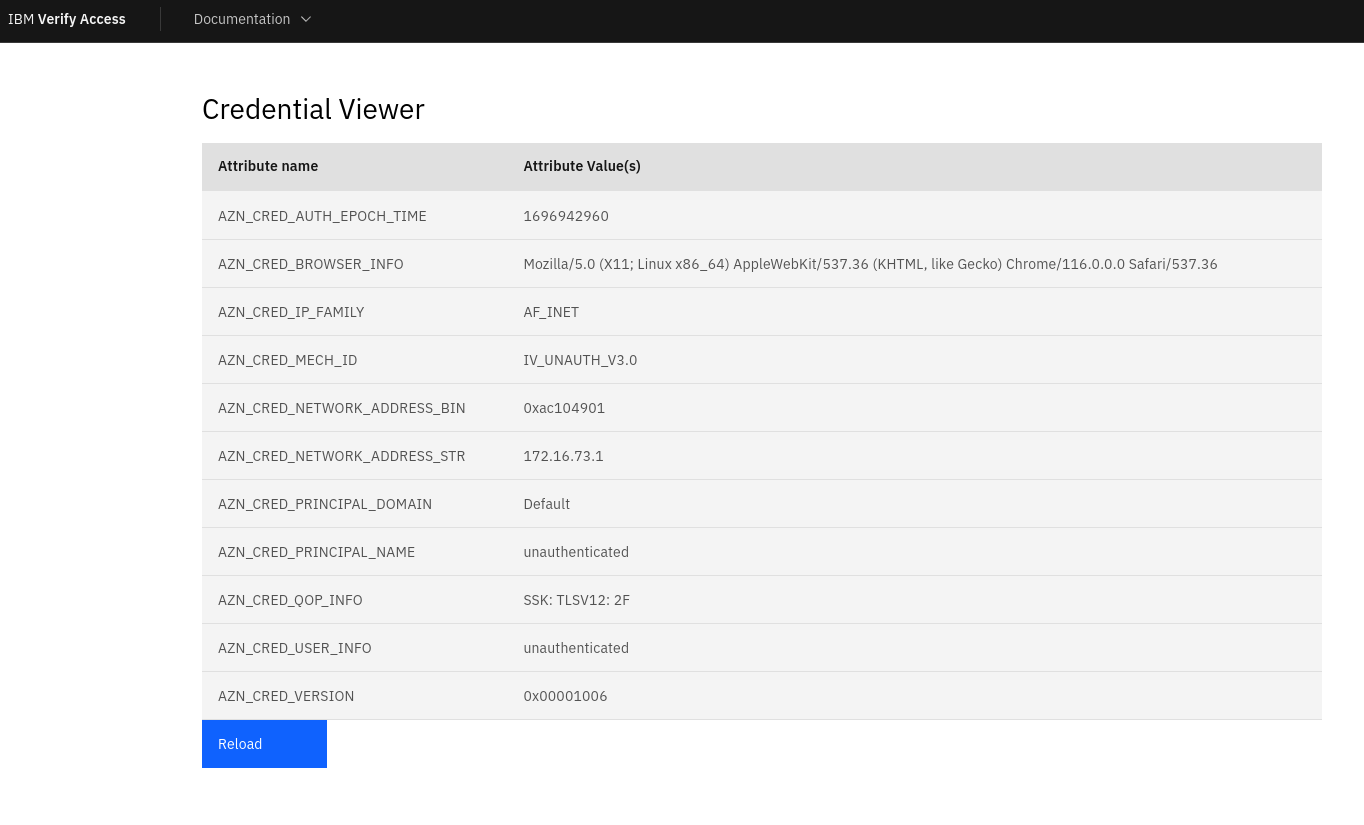
Example : authenticated
When you are logged in, the credential viewer shows more attributes: