ISAM SPNEGO configuration
SPNEGO challenge when reverse dns lookup does not match the requested hostname. The challenge with SPNEGO or rather the Kerberos implementation on ISAM is that it depends on reverse DNS lookups (on the ip address) by default to verify that the hostname you want to connect to.
This means that even though you have keytabs for the hostname you connect to, the SSO will fail if the reverse dns lookup returns another hostname for that IP address.
Typically , you’ll see errors in your log similar to this :
483 2019-09-10-17:13:53.304+02:00I----- 0x30923082 webseald ERROR bst general amstli.c 2764 0x7f55c50de700 -- HPDST0130E The security service function gss_accept_sec_context returned the error 'Request ticket server HTTP/realservername.domain.com@AD not found in keytab (ticket kvno 3)' (code 0x96c73a23/-1765328349).
Resolution
2 solutions exist. The first one, changing DNS , is sometimes difficult to explain (because not all Kerberos implementations are equal, and SPNEGO works for other servers, the client may not understand why it’s necessary).
So there is a second solution, by using some of the newer kerberos parameters (NEW in Kerberos 1.10).
So this may not be possible on your ISAM version ! I am using 9.0.6 in this case, which comes with Kerberos 1.12 .
DNS
The old way to resolve this, is to make sure the reverse dns lookup for your ip address returns the hostname of your WebSeal proxy (the one users connect to). In this way, you just need the 1 SPN in your keytab.**
Configuration with additional keytabs
You need to have a keytab that contains the hostname for the url the user accesses, and the hostname for all backend servers (ie. what’s in the reverse dns lookup and A records) as SPN.
You can combine them in ISAM.
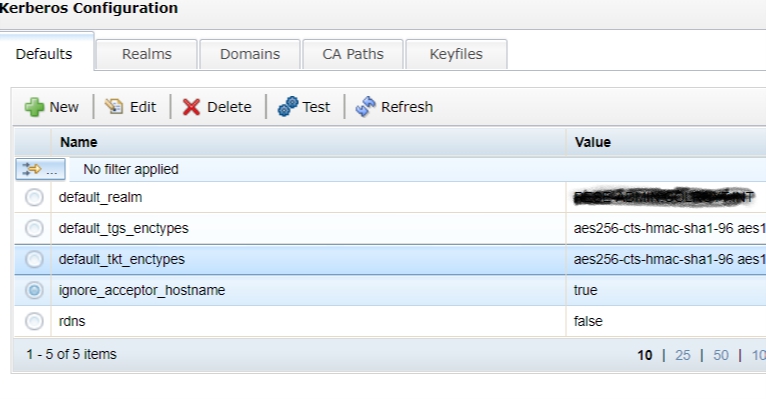
Then , you can add these 2 parameters to the Defaults section in Kerberos configuration. Rdns is false does not really seem to have a lot of effect, to be honest, but ignore_acceptor_hostname is the golden ticket here.
ignore_acceptor_hostname = true
rdns = false
References
https://web.mit.edu/kerberos/krb5-1.12/doc/admin/conf_files/krb5_conf.html
https://www.ibm.com/developerworks/community/wikis/home?lang=en#!/wiki/W746177d414b9_4c5f_9095_5b8657ff8e9d/page/Information%20and%20Guides%20for%20Kerberos%20SSO